Introduction
HAPI FHIR is an open source implementation of the HL7 FHIR standard for healthcare interoperability.
The easiest way to get started with HAPI FHIR is to use the HAPI FHIR JPA Server Starter Project.
In previous posts, we have worked to augment the HAPI FHIR JPA Server Starter Project in order to demonstrate secure access to FHIR resources.
Including:
- Support for OpenID Connect and OAuth 2.0 (e.g., SMART on FHIR)
See: HAPI FHIR AU Starter Project
In this post, we'll enable TLS in HAPI FHIR's embedded web server and ensure that all PostgreSQL clients use encrypted connections.
HAPI FHIR
Enable TLS
HAPI FHIR relies on the underlying web server for TLS encryption.
All embedded web servers supported by Spring Boot can be configured to secure connections with TLS (SSL) by using the server.ssl.* properties.
For example:
services:
hapi-fhir:
container_name: hapi-fhir
build:
context: ./services/hapi-fhir
dockerfile: Dockerfile
restart: unless-stopped
ports:
- 6443:8443
environment:
SERVER_SSL_ENABLED: true
SERVER_SSL_KEY_STORE_TYPE: PKCS12
SERVER_SSL_KEY_STORE: file:/keystore/keystore.p12
SERVER_SSL_KEY_STORE_PASSWORD: secret
SERVER_SSL_KEY_ALIAS: tomcat
SERVER_PORT: 8443
SPRING_DATASOURCE_URL: jdbc:postgresql://postgres:5432/${HAPI_FHIR_DB}
SPRING_DATASOURCE_USERNAME: ${POSTGRES_USER}
SPRING_DATASOURCE_PASSWORD: ${POSTGRES_PASSWORD}
SPRING_DATASOURCE_DRIVER_CLASS_NAME: org.postgresql.Driver
SPRING_JPA_PROPERTIES_HIBERNATE_DIALECT: ca.uhn.fhir.jpa.model.dialect.HapiFhirPostgresDialect
SPRING_JPA_PROPERTIES_SEARCH_ENABLED: false
env_file:
- ./.env
volumes:
- '${PWD}/certs/keystore.p12:/keystore/keystore.p12'
configs:
- source: hapi
target: /app/config/application.yaml
depends_on:
postgres:
condition: service_healthy
keycloak.au.localhost:
condition: service_healthy
networks:
- hapi_fhir_network
...
configs:
hapi:
file: ./hapi.application-enable-tls.yaml
See: docker-compose.yml
Access to a keystore file containing the server certificate and private key is also required. You can use openssl to create a PKCS12 keystore.
For example:
openssl pkcs12 -export -in cert.pem -inkey key.pem -out keystore.p12 -name tomcat -password pass:secret
PostgreSQL
Enable TLS
Support for encrypted connections is enabled by setting the ssl parameter to on. The server will listen for both normal and secure connections on the same port.
Connecting clients can be required to use encrypted connections by setting the environment variable PGSSLMODE to require.
For example:
services:
postgres:
container_name: postgres
...
command: >
-c ssl=on
-c ssl_cert_file=/var/lib/postgresql/server.crt
-c ssl_key_file=/var/lib/postgresql/server.key
environment:
POSTGRES_DB: ${POSTGRES_DB}
POSTGRES_USER: ${POSTGRES_USER}
POSTGRES_PASSWORD: ${POSTGRES_PASSWORD}
PGSSLMODE: require
env_file:
- ./.env
volumes:
- '${PWD}/certs/cert.pem:/var/lib/postgresql/server.crt'
- '${PWD}/certs/key.pem:/var/lib/postgresql/server.key'
- postgres_data:/var/lib/postgresql/data
...
PostgreSQL also requires access to the files containing the server certificate and private key.
Note: On Unix and macOS systems the cert and key file permissions must disallow any access to world or group.
For example:
sudo chmod 600 *.pem
We can check that the connections to PostgreSQL are secure by running the following query:
select pg_ssl.pid, pg_ssl.ssl, pg_ssl.version,
pg_sa.backend_type, pg_sa.usename, pg_sa.client_addr
from pg_stat_ssl pg_ssl
join pg_stat_activity pg_sa
on pg_ssl.pid = pg_sa.pid;
In pgAdmin:
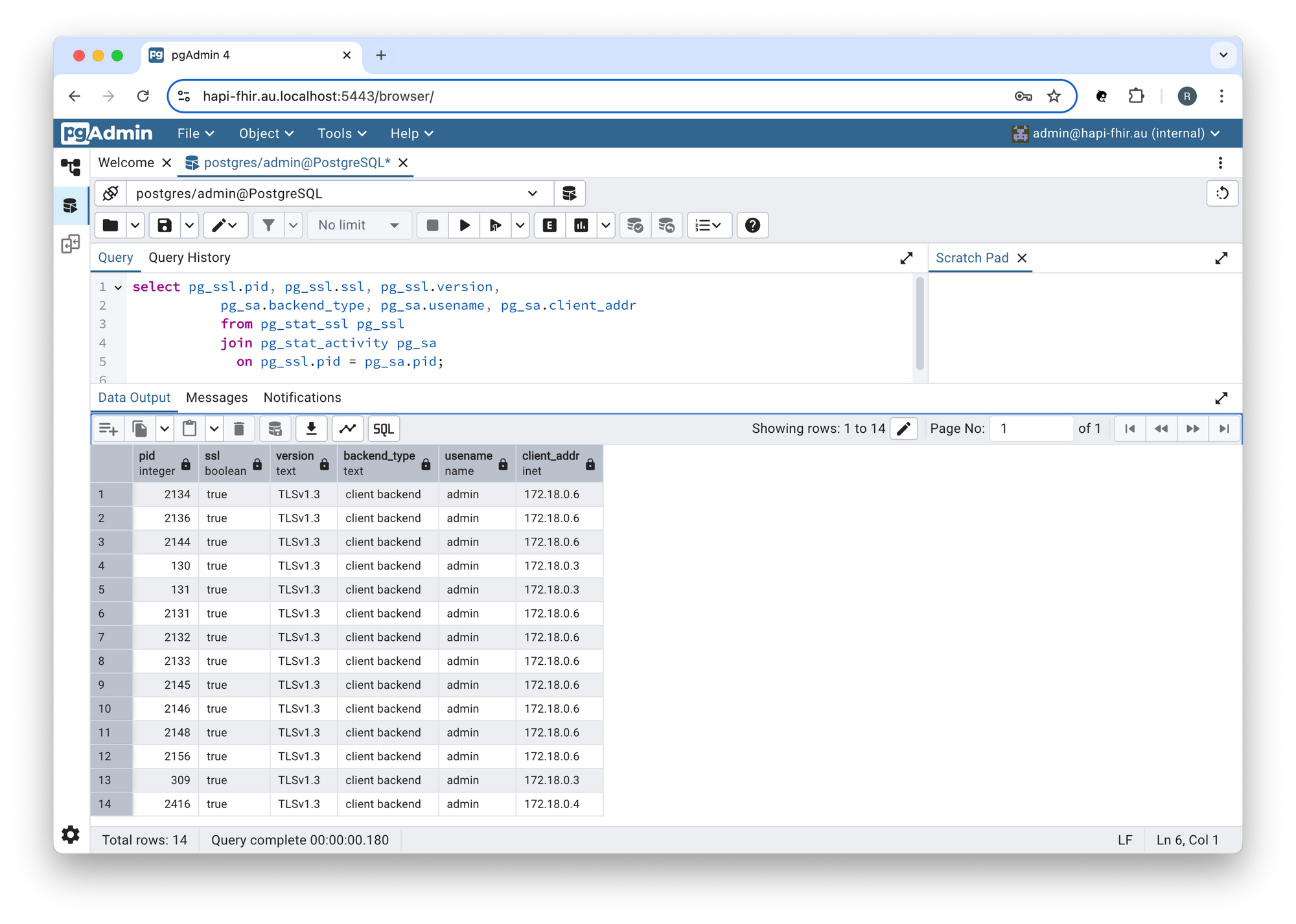
We can obtain HAPI FHIR's IP Address using the following command:
docker inspect -f '{{range .NetworkSettings.Networks}}{{.IPAddress}}{{end}}' hapi-fhir
You should see something like:
172.18.0.6
Source Code
- GitHub: HAPI FHIR AU Starter Project
Resources
- HAPI FHIR: Website
- HAPI FHIR: Documentation
- HAPI FHIR AU docs: Working with mkcert
- PostgreSQL: Documentation