In a previous post I wrote about how to build Flowable ('build from source') and then create a Docker image.
In this post, we'll configure Flowable to use OpenLDAP.
OpenLDAP
Getting Started
The easiest way to get started with OpenLDAP is to use a Docker image, for example:
docker pull osixia/openldap:1.3.0
docker run --detach --name openldap \
--publish 10389:389 \
--publish 10636:636 \
--volume ~/workspace/Robinyo/serendipity:/serendipity \
--env LDAP_ORGANISATION="flowable" \
--env LDAP_DOMAIN="flowable.org" \
--env LDAP_ADMIN_PASSWORD="secret" \
osixia/openldap:1.3.0
When you run the image it will create the organisation (flowable), create the domain (flowable.org) and set the LDAP administrator's password (secret).
Let's check and see:
docker exec openldap ldapsearch \
-x -H ldap://localhost \
-b dc=flowable,dc=org \
-D "cn=admin,dc=flowable,dc=org" \
-w secret
You should see ouput like:
# extended LDIF
#
# LDAPv3
# base <dc=flowable,dc=org> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# flowable.org
dn: dc=flowable,dc=org
objectClass: top
objectClass: dcObject
objectClass: organization
o: flowable
dc: flowable
# admin, flowable.org
dn: cn=admin,dc=flowable,dc=org
objectClass: simpleSecurityObject
objectClass: organizationalRole
cn: admin
description: LDAP administrator
userPassword:: e1NTSEF9QXhWK0MvL1JEK2xsU1g2dG1CemRybGFwRW9OdzVwbTI=
# search result
search: 2
result: 0 Success
# numResponses: 3
# numEntries: 2
Flowable.ldif
I created an ldif (LDAP Data Interchange Format) file with two containers (users and groups) and one user (flowable):
# Users root
dn: ou=users, dc=flowable,dc=org
ou: users
description: All users in the organisation
objectclass: organizationalUnit
objectClass: extensibleObject
objectClass: top
# Groups root
dn: ou=groups, dc=flowable,dc=org
ou: groups
description: All groups in the organisation
objectclass: organizationalUnit
objectClass: extensibleObject
objectClass: top
# Actual users
dn: cn=Administrator, ou=users,dc=flowable,dc=org
objectclass: inetOrgPerson
cn: Administrator
sn:
mail: admin@serendipity.org.au
uid: flowable
userPassword: dGVzdA==
Note: The userPassword must be Base64 encoded.
Then I used ldapadd to update OpenLDAP:
docker exec openldap ldapadd \
-x -H ldap://localhost \
-D "cn=admin,dc=flowable,dc=org" \
-w secret \
-f ./serendipity/flowable/flowable.ldif
If we search the directory again:
docker exec openldap ldapsearch \
-x -H ldap://localhost \
-b dc=flowable,dc=org \
-D "cn=admin,dc=flowable,dc=org" \
-w secret
You should see ouput like:
# extended LDIF
#
# LDAPv3
# base <dc=flowable,dc=org> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# flowable.org
dn: dc=flowable,dc=org
objectClass: top
objectClass: dcObject
objectClass: organization
o: flowable
dc: flowable
# admin, flowable.org
dn: cn=admin,dc=flowable,dc=org
objectClass: simpleSecurityObject
objectClass: organizationalRole
cn: admin
description: LDAP administrator
userPassword:: e1NTSEF9TFFqN05uYzcydWVpcUREUHdxQ0xoMlNwRHB5V2FzaDY=
# users, flowable.org
dn: ou=users,dc=flowable,dc=org
ou: users
description: All users in the organisation
objectClass: organizationalUnit
objectClass: extensibleObject
objectClass: top
# groups, flowable.org
dn: ou=groups,dc=flowable,dc=org
ou: groups
description: All groups in the organisation
objectClass: organizationalUnit
objectClass: extensibleObject
objectClass: top
# Flowable, users, flowable.org
dn: cn=Flowable,ou=users,dc=flowable,dc=org
objectClass: inetOrgPerson
cn: Flowable
sn: Administrator
uid: flowable
userPassword: dGVzdA==
# search result
search: 2
result: 0 Success
# numResponses: 6
# numEntries: 5
You can also use an LDAP Browser to manage your directory:
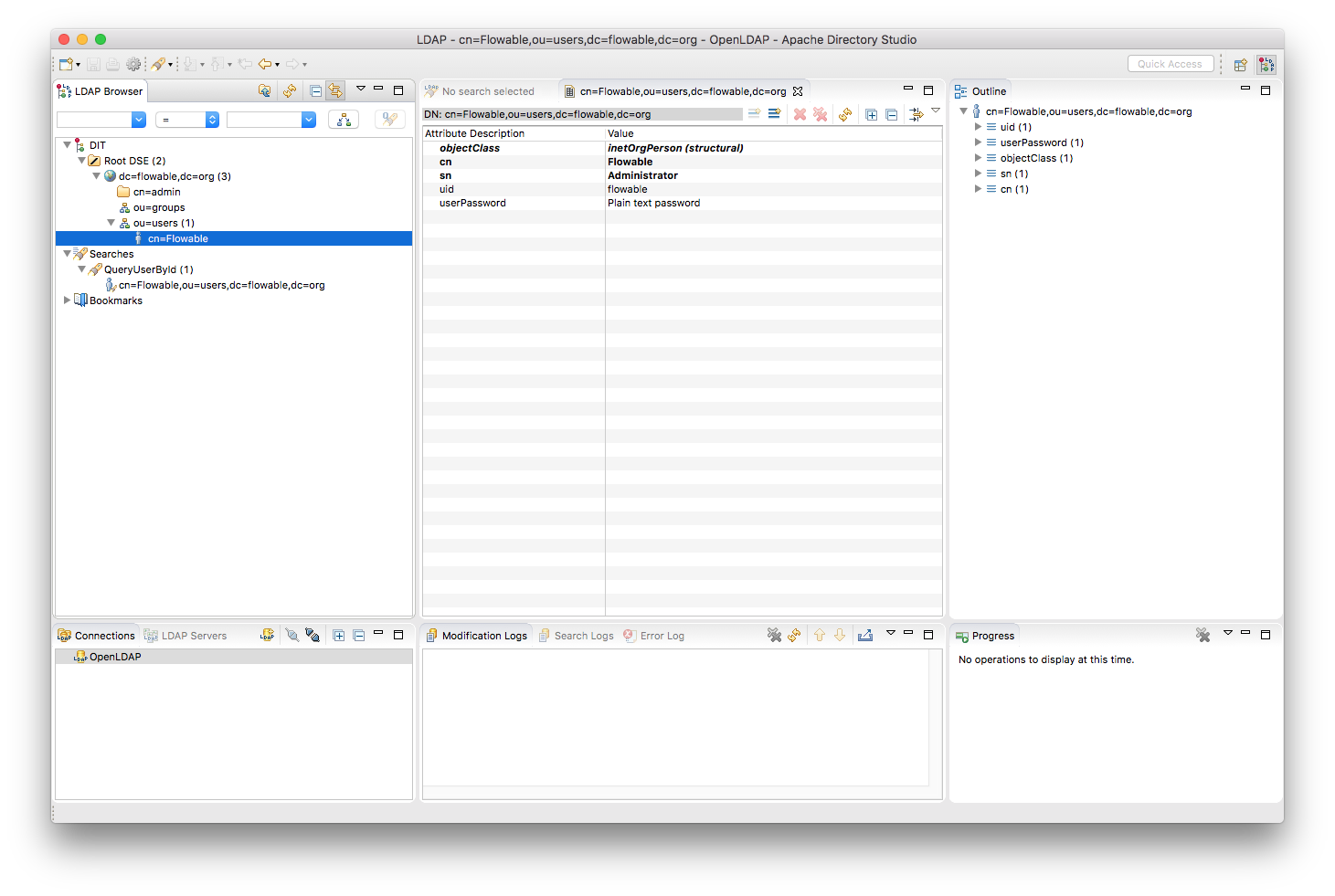
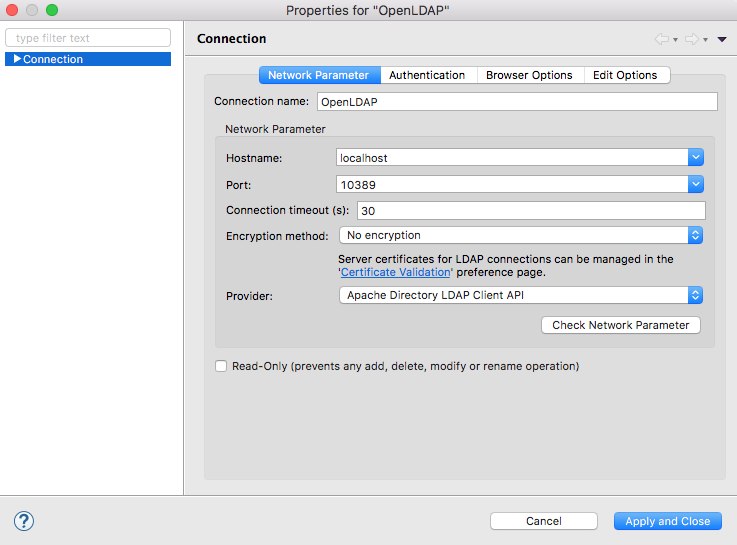
Network settings:
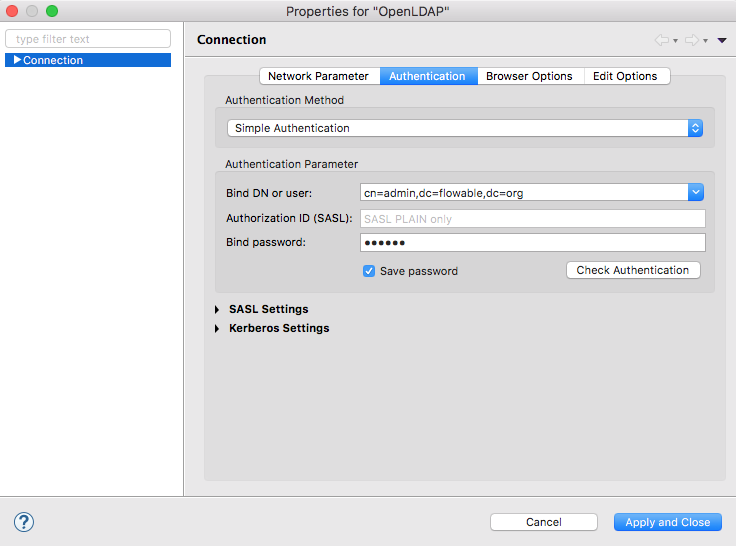
Authentication settings:
Flowable 6.5.0
Configuration Properties
We can use an environment file to pass properties to the Docker container:
#
# LDAP
#
FLOWABLE_IDM_LDAP_ENABLED=true
FLOWABLE_IDM_LDAP_SERVER=ldap://host.docker.internal
# FLOWABLE_IDM_LDAP_SERVER=ldap://localhost
FLOWABLE_IDM_LDAP_PORT=10389
FLOWABLE_IDM_LDAP_USER=cn=admin,dc=flowable,dc=org
FLOWABLE_IDM_LDAP_PASSWORD=secret
FLOWABLE_IDM_LDAP_BASE_DN=dc=flowable,dc=org
FLOWABLE_IDM_LDAP_USER_BASE_DN=ou=users,dc=flowable,dc=org
FLOWABLE_IDM_LDAP_GROUP_BASE_DN=ou=groups,dc=flowable,dc=org
FLOWABLE_IDM_LDAP_QUERY_USER_BY_ID=(&(objectClass=inetOrgPerson)(uid={0}))
FLOWABLE_IDM_LDAP_QUERY_USER_BY_FULL_NAME_LIKE=(&(objectClass=inetOrgPerson)(|({0}=*{1}*)({2}=*{3}*)))
FLOWABLE_IDM_LDAP_QUERY_ALL_USERS=(objectClass=inetOrgPerson)
FLOWABLE_IDM_LDAP_QUERY_GROUPS_FOR_USER=(&(objectClass=groupOfUniqueNames)(uniqueMember={0}))
FLOWABLE_IDM_LDAP_QUERY_ALL_GROUPS=(objectClass=groupOfUniqueNames)
FLOWABLE_IDM_LDAP_QUERY_GROUP_BY_ID=(&(objectClass=groupOfUniqueNames)(uniqueId={0}))
FLOWABLE_IDM_LDAP_ATTRIBUTE_USER_ID=uid
FLOWABLE_IDM_LDAP_ATTRIBUTE_FIRST_NAME=cn
FLOWABLE_IDM_LDAP_ATTRIBUTE_LAST_NAME=sn
FLOWABLE_IDM_LDAP_ATTRIBUTE_EMAIL=mail
FLOWABLE_IDM_LDAP_ATTRIBUTE_GROUP_ID=cn
FLOWABLE_IDM_LDAP_ATTRIBUTE_GROUP_NAME=cn
FLOWABLE_IDM_LDAP_CACHE_GROUP_SIZE=10000
FLOWABLE_IDM_LDAP_CACHE_GROUP_EXPIRATION=180000
#
# DEFAULT ADMINISTRATOR ACCOUNTS
#
FLOWABLE_IDM_APP_ADMIN_USER_ID=flowable
FLOWABLE_IDM_APP_ADMIN_PASSWORD=test
FLOWABLE_IDM_APP_ADMIN_FIRST_NAME=Flowable
FLOWABLE_IDM_APP_ADMIN_LAST_NAME=Administrator
FLOWABLE_IDM_APP_ADMIN_EMAIL=admin@flowable.org
FLOWABLE_COMMON_APP_IDM_ADMIN_USER=flowable
FLOWABLE_COMMON_APP_IDM_ADMIN_PASSWORD=test
Note: If you don't properly configure the default Administrator accounts you may be able to sign in to Flowable's Identity Management application, however, you won't be able to sign in to the other Flowable UI applications.
Launch Flowable
To launch the flowable/all-in-one 6.5.0 image:
docker pull flowable/all-in-one:6.5.0
docker run -d --name flowable \
-p 8080:8080 \
--env-file ./ldap-env.txt \
flowable/all-in-one:6.5.0
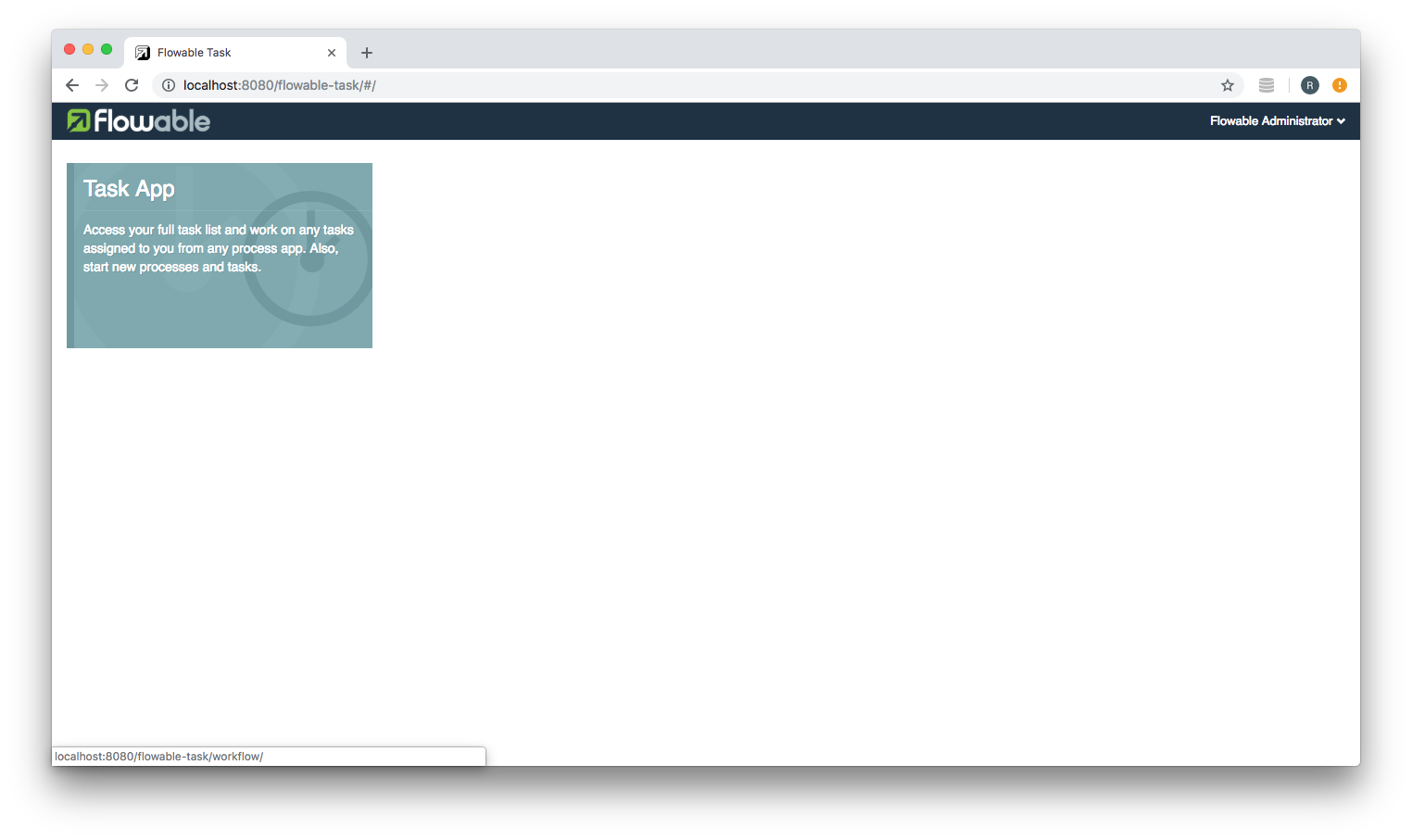
Navigate to the Flowable Task application: http://localhost:8080/flowable-task and you will be redirected to Flowable's Identity Management application. Sign in using the default user id: flowable and password: test

You will then be redirected back to the Flowable Task application:
Note: You can use Chrome's Developer Tools to check the request URL, headers and form data:
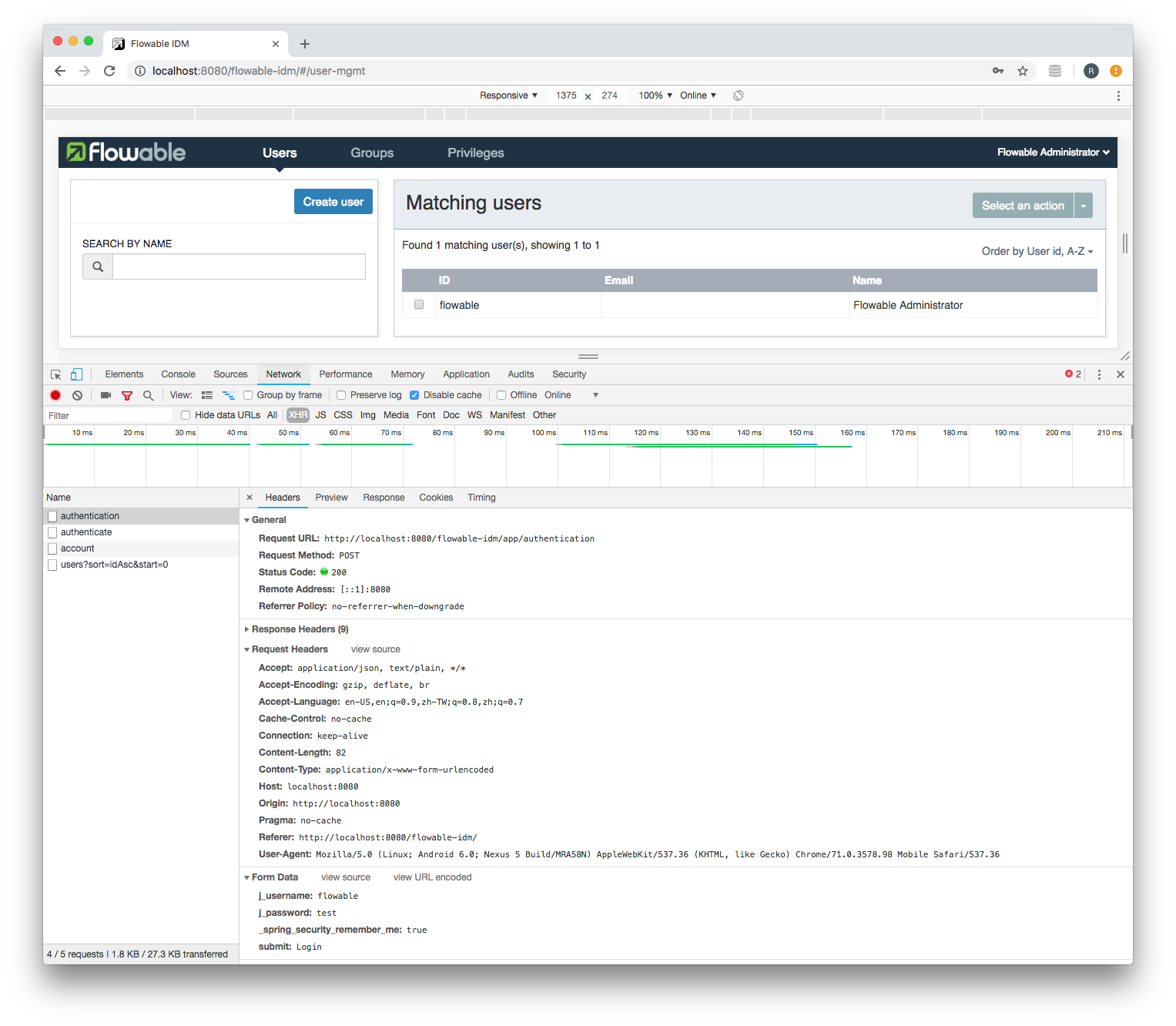
Source Code:
- GitHub: Serendipity
References:
- Flowable docs: LDAP
- GitHub: A sample users.ldif
- DigitalOcean: How To Use LDIF Files to Make Changes to an OpenLDAP System
- Spring docs: Externalized Configuration
- ApacheDS: Apache Directory Studio
- Docker docs: I want to connect from a container to a service on the host